

Jung Yeon-Je/Getty Photos
The US Pentagon, the FBI, and the Division of Homeland Safety on Friday uncovered a North Korean hacking operation and offered technical particulars for seven items of malware used in the marketing campaign.
The US Cyber Nationwide Mission Power, an arm of the Pentagon’s US Cyber Command, mentioned on Twitter that the malware is “at present used for phishing & distant entry by [North Korean government] cyber actors to conduct criminal activity, steal funds & evade sanctions.” The tweet linked to a put up on VirusTotal, the Alphabet-owned malware repository, that offered cryptographic hashes, file names, and different technical particulars that may assist defenders determine compromises contained in the networks they shield.
Malware attributed to #NorthKorea by @FBI_NCIJTF simply launched right here: https://t.co/cBqSL7DJzI. This malware is at present used for phishing & distant entry by #DPRK cyber actors to conduct criminal activity, steal funds & evade sanctions. #HappyValentines @CISAgov @DHS @US_CYBERCOM
— USCYBERCOM Malware Alert (@CNMF_VirusAlert) February 14, 2020
An accompanying advisory from the DHS’s Cybersecurity and Infrastructure Safety Company mentioned the marketing campaign was the work of Hidden Cobra, the government’s identify for a hacking group sponsored by the North Korean Government. Many safety researchers in the non-public sector use different names for the group, together with Lazarus and Zinc. Six of the seven malware households had been uploaded to VirusTotal on Friday. They included:
- Bistromath, a full-featured distant entry trojan and implant that performs system surveys, file uploads and downloads, course of and command executions, and monitoring of microphones, clipboards, and screens
- Slickshoes, a “dropper” that masses, however doesn’t really execute, a “beaconing implant” that may do most of the similar issues Bistromath does
- Hotcroissant, a full-featured beaconing implant that additionally does most of the similar issues listed above
- Artfulpie, an “implant that performs downloading and in-memory loading and execution of DLL recordsdata from a hardcoded url”
- Buttetline, one other full-featured implant, however this one makes use of faux a faux HTTPS scheme with a modified RC4 encryption cipher to stay stealthy
- Crowdedflounder, a Home windows executable that’s designed to unpack and execute a Distant Entry Trojan into pc reminiscence
However wait… there’s extra
Friday’s advisory from the Cybersecurity and Infrastructure Safety Company additionally offered further particulars for the beforehand disclosed Hoplight, a household of 20 recordsdata that act as a proxy-based backdoor. Not one of the malware contained solid digital signatures, a way that’s customary amongst extra superior hacking operations that makes it simpler to bypass endpoint safety protections.
Costin Raiu, director of the International Analysis and Evaluation Workforce at Kaspersky Lab, posted a picture on Twitter that confirmed the connection between the malware detailed on Friday with malicious samples the Moscow-based safety agency has recognized in different campaigns attributed to Lazarus.
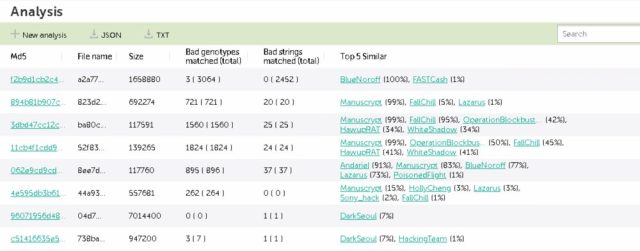
Kaspersky Lab
Friday’s joint advisory is a part of a comparatively new method by the federal government to publicly determine foreign-based hackers and the campaigns they perform. Beforehand, government officers principally steered away from attributing particular hacking actions to particular governments. In 2014, that method started to change when the FBI publicly concluded that the North Korean government was behind the extremely harmful hack of Sony Photos a yr earlier. In 2018, the Division of Justice indicted a North Korean agent for allegedly finishing up the Sony hack and unleashing the WannaCry ransomware worm that shut down computer systems worldwide in 2017. Final yr, the US Treasury sanctioned three North Korean hacking teams extensively accused of assaults that focused essential infrastructure and stole hundreds of thousands of {dollars} from banks in cryptocurrency exchanges.
As Cyberscoop identified, Friday marked the primary time that the US Cyber Command recognized a North Korean hacking operation. One cause for the change: though the North Korean government hackers usually use much less superior malware and methods than counterparts from different nations, the assaults are rising more and more refined. Information companies together with Reuters have cited a United Nations report from final August that estimated North Korean hacking of banks and cryptocurrency exchanges has generated $2 billion for the nation’s weapons of mass destruction packages.