

One of the highest-impact Windows vulnerabilities patched this yr is now under active exploitation by malicious hackers, Microsoft warned in a single day, in a growth that places growing stress on laggards to replace now.
CVE-2020-1472, because the vulnerability is tracked, permits hackers to immediately take management of the Active Listing, a Windows server useful resource that acts as an omnipotent gatekeeper for all machines related to a community. Researchers have dubbed the vulnerability Zerologon, as a result of it permits attackers with solely minimal entry to a weak community to login to the Active Listing by sending a string of zeros in messages that use the Netlogon protocol.
Zerologon carries a important severity ranking from Microsoft in addition to a most of 10 under the Frequent Vulnerability Scoring System. Regardless of the excessive ranking, the escalation-of-privileges vulnerability acquired scant, if any, consideration when Microsoft patched it in August, and Microsoft deemed the possibilities of precise exploitation “much less probably.”
The safety world lastly took discover final week with the discharge of a number of proof-of-concept exploits and an in depth writeup, which demonstrated severity of the vulnerability and the relative ease in exploiting it.
All palms on deck
On Wednesday night, Microsoft issued a sequence of tweets that Zerologon was now being exploited within the wild.
“Microsoft is actively monitoring menace actor exercise utilizing exploits for the CVE-2020-1472 Netlogon EoP vulnerability, dubbed Zerologon,” Microsoft representatives wrote. “Now we have noticed assaults the place public exploits have been included into attacker playbooks.”
Microsoft 365 clients can consult with the menace analytics report we printed in Microsoft Defender Safety Heart. The menace analytics report accommodates technical particulars, mitigations, and detection particulars designed to empower SecOps to detect and mitigate this menace.
— Microsoft Safety Intelligence (@MsftSecIntel) September 24, 2020
The corporate supplied a number of digital signatures of recordsdata used within the assaults, but it surely didn’t publicly present further particulars. Microsoft has printed a menace analytics report that’s designed to assist directors assess the vulnerability of their networks, but it surely’s accessible solely to Workplace 365 subscribers. For everybody else, the most effective useful resource is this white paper from Secura, the safety agency that found Zerologon. Microsoft representatives didn’t reply to an e-mail asking for a duplicate of the analytics report.
Crown jewels
It’s exhausting to overstate the severity of an exploit that makes it doable to take management of an Active Listing utilizing a number of dozen strains of code. Active Directories (and the area controller servers they run on) are the assets most cherished by ransomware attackers. With management over the central provisioning listing, they’ll infect complete fleets of machines inside minutes. Nation-sponsored hackers performing surgical-precision espionage campaigns additionally prize such entry as a result of it permits them to manage particular community assets of curiosity.
Each varieties of attackers typically start hacks by compromising a pc with low-level privileges on a community, typically by tricking an worker into clicking on a malicious hyperlink or file or by coming into a password on a phishing web page. It may possibly typically take weeks or months to escalate low-level privileges to these wanted to put in malware or execute instructions. In sure circumstances, Zerologon can enable an attacker with this variety of toehold to virtually immediately achieve management of the Active Listing.
There can also be methods to exploit Zerologon instantly from the Web with no earlier entry. Web searches like this one and this one present greater than 33,000 and three million networks are exposing area controllers and Distant Process Name login servers to the general public Web. Within the occasion a single community is exposing each assets, the mixture might depart a community large open with no different necessities.
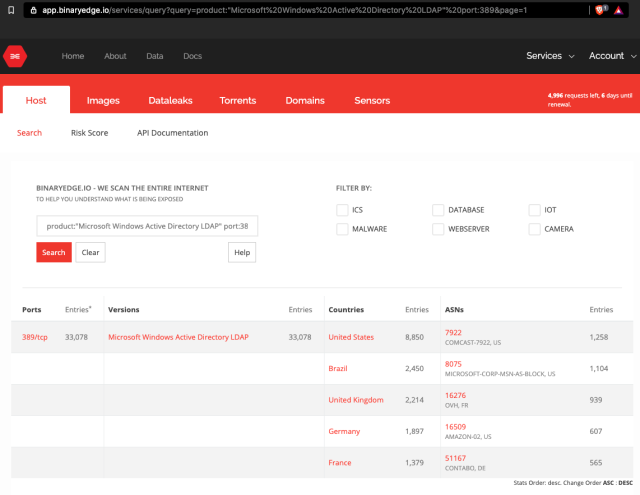
Binary Edge
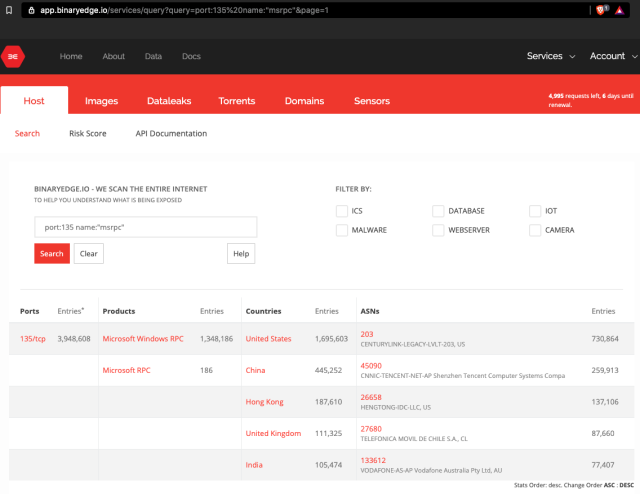
Binary Edge
The danger posed by Zerologon isn’t simply that of going through a catastrophic hack. There’s additionally the menace of making use of a patch that breaks a community’s most delicate useful resource. Late final week, the cybersecurity arm of the Division of Homeland Safety mandated businesses to both apply the patch by Monday night time or take away area controllers from the Web.
With phrase lower than three days later that exploits are within the wild, it’s clear there was good cause for the directive.