

Because the world’s prime oil producers ready for a weeklong assembly earlier this month to plan a response to slumping costs of crude, espionage hackers commenced a subtle spearphishing marketing campaign that was targeting US-based power firms. The aim: set up a infamous trojan that siphoned their most delicate communications and information.
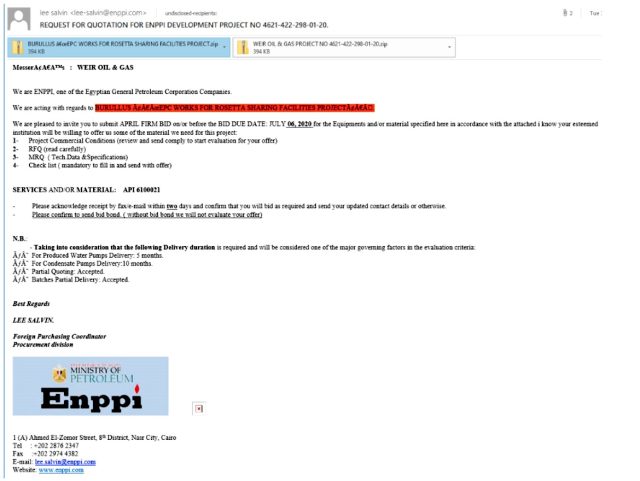
Setting the marketing campaign aside, the emails have been largely free of the typos, damaged grammar, and different sloppiness which might be typical phishes. The emails additionally mirrored a sender who was well-acquainted with the enterprise of power manufacturing. A barrage of emails that began on March 31, as an illustration, purported to return from Engineering for Petroleum and Course of Industries, a actual Egyptian state oil firm.
Not your father’s spear-phishing
The sender invited the recipient to submit a bid for gear and supplies as half of a actual ongoing mission, recognized as the Rosetta Sharing Amenities Mission, on behalf of Burullus, a fuel three way partnership that’s half-owned by one other Egyptian state oil firm. The e-mail, which was despatched to about 150 oil and fuel firms over a week beginning on March 31, connected two recordsdata that masqueraded as bidding situations, types, and a request for proposal. The comparatively small quantity of emails demonstrates a slim focusing on of the rigorously crafted marketing campaign. In contrast, many phishing campaigns non-discriminately ship tens of 1000’s of emails.
Bitdefender
“To somebody within the oil & fuel business, who has data about these initiatives, the e-mail and the data inside might sound sufficiently convincing to open the attachments,” researchers from safety agency Bitdefender wrote in a put up revealed on Tuesday.
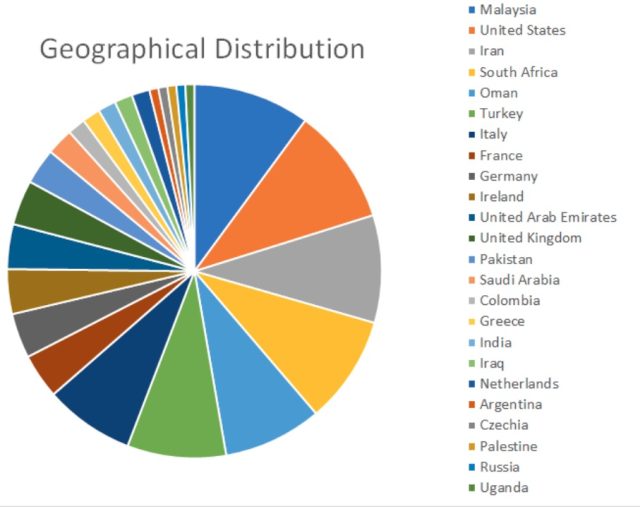
Probably the most-targeted firms have been situated in Malaysia, america, Iran, South Africa, and Oman.
Bitdefender
A second marketing campaign began on April 12. It despatched an e-mail asking recipients to finish a doc recognized as an Estimated Port Disbursement Account wanted for the chemical and oil tanker named MT Sinar Maluku. Not solely was that a actual vessel registered underneath the Indonesian flag, it had left its port on April 12 and was anticipated to achieve its vacation spot two days later. The e-mail was despatched to 18 firms, 15 of which have been cargo firms within the Philippines.
“This e-mail serves as one other instance of the size to which attackers will go to get their information straight, make the e-mail appear respectable, and particularly target a vertical.
Pandemic-induced glut
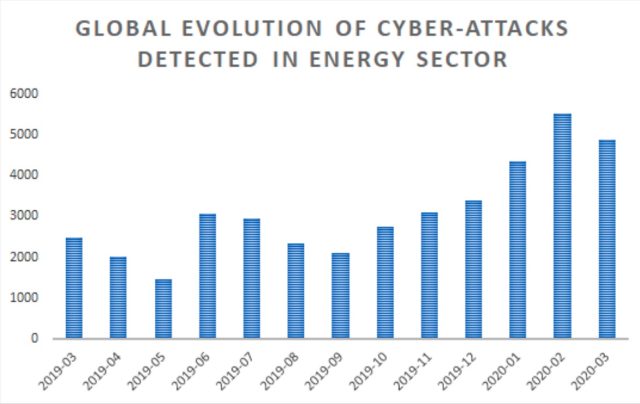
The campaigns are probably an try to realize intently guarded details about the present negotiations between Russia, Saudi Arabia, and different oil producers struggling with a glut of crude ensuing from the coronavirus pandemic. Bitdefender stated that is hardly the primary time firms on this business have been focused. The safety agency has been monitoring a run of cyber assaults on power firms over the previous 12 months. Since September, the quantity has elevated each month and reached a peak in February with greater than 5,000. There have been greater than 13,000 assaults this 12 months.
Each of the latest campaigns ship recordsdata that set up Agent Tesla, a malware-as-a-service providing that expenses varied costs primarily based on totally different licensing fashions. The trojan, which has been out there since 2014, has a selection of capabilities that embrace involving “stealth, persistence and safety evasion strategies that finally allow it to extract credentials, copy clipboard information, carry out display screen captures, form-grabbing, and keylogging performance, and even gather credentials for a selection of put in functions.”
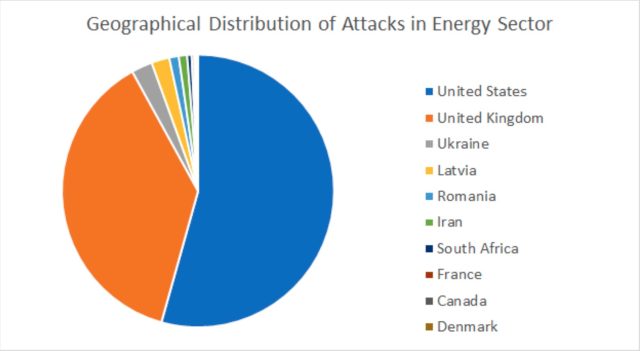
Corporations within the US have been focused essentially the most, adopted by the UK, Ukraine, and Latvia.
“What’s attention-grabbing is that, till now, it has not been related with campaigns focusing on the oil & fuel vertical,” Bitdefender researchers added.
The marketing campaign gives a reminder that, regardless of the rising consciousness of phishing assaults, they stay one of the best methods for attackers to realize a foothold in focused firms. Even when phishing emails include misspellings, grammatical errors, and different flaws, recipients typically rightly assume these are the outcomes of senders writing in a second language. Phishes as properly crafted as these ones stand a fair higher chance of success.