

Aurich Lawson | Getty Photographs
Beforehand, on “Weekend Initiatives for Homelab Admins With Management Points,” we created our own dynamically updating DNS and DHCP setup with bind and dhcpd. We laughed. We cried. We hurled. Bonds had been cast, by no means to be damaged. And I hope all of us took slightly one thing particular away from the journey—particularly, a dynamically updating DNS and DHCP setup. Which we’re now going to place to make use of!
When you’re becoming a member of us contemporary, with out having gone by way of the earlier half and desirous to observe this tutorial, howdy! There may be some components which can be harder to finish with no native occasion of bind (or different authoritative resolver suitable with nsupdate). We’ll discuss extra about this once we get there, however simply know that if you wish to pause and go do half one first, you will have a neater time following alongside.
The short model: A LetsEncrypt of our own
This text will stroll by way of the method of putting in step-ca, a standalone certificates authority-in-a-box. We’ll then configure step-ca with an ACME provisioner—that is Automated Certificates Administration Atmosphere, the expertise that underpins LetsEncrypt and facilitates the automated provisioning, renewal, and revocation of SSL/TLS certificates.
After we get step-ca listening for incoming ACME requests, we’ll discuss by way of the methods to get the self-hosted companies on your LAN-speaking ACME to allow them to begin routinely requesting certificates from our step-ca certificates authority—similar to how LetsEncrypt works.
I am going to focus solely on utilizing acme.sh for requesting and renewing certs on shoppers as a result of it is the instrument I am most aware of. However every little thing we do must be doable with any ACME consumer, so when you’re extra comfortable with certbot or dehydrated no matter, be happy to make use of that on your shoppers. The directions must be fairly straightforward to adapt.
I didn’t perceive any of that—we’re doing what now?
So you understand how you put in a brand new self-hosted factor on your LAN, and whenever you log into its internet interface, you get a “your connection is not safe” warning as a result of the factor you simply put in is utilizing a self-signed TLS certificates?
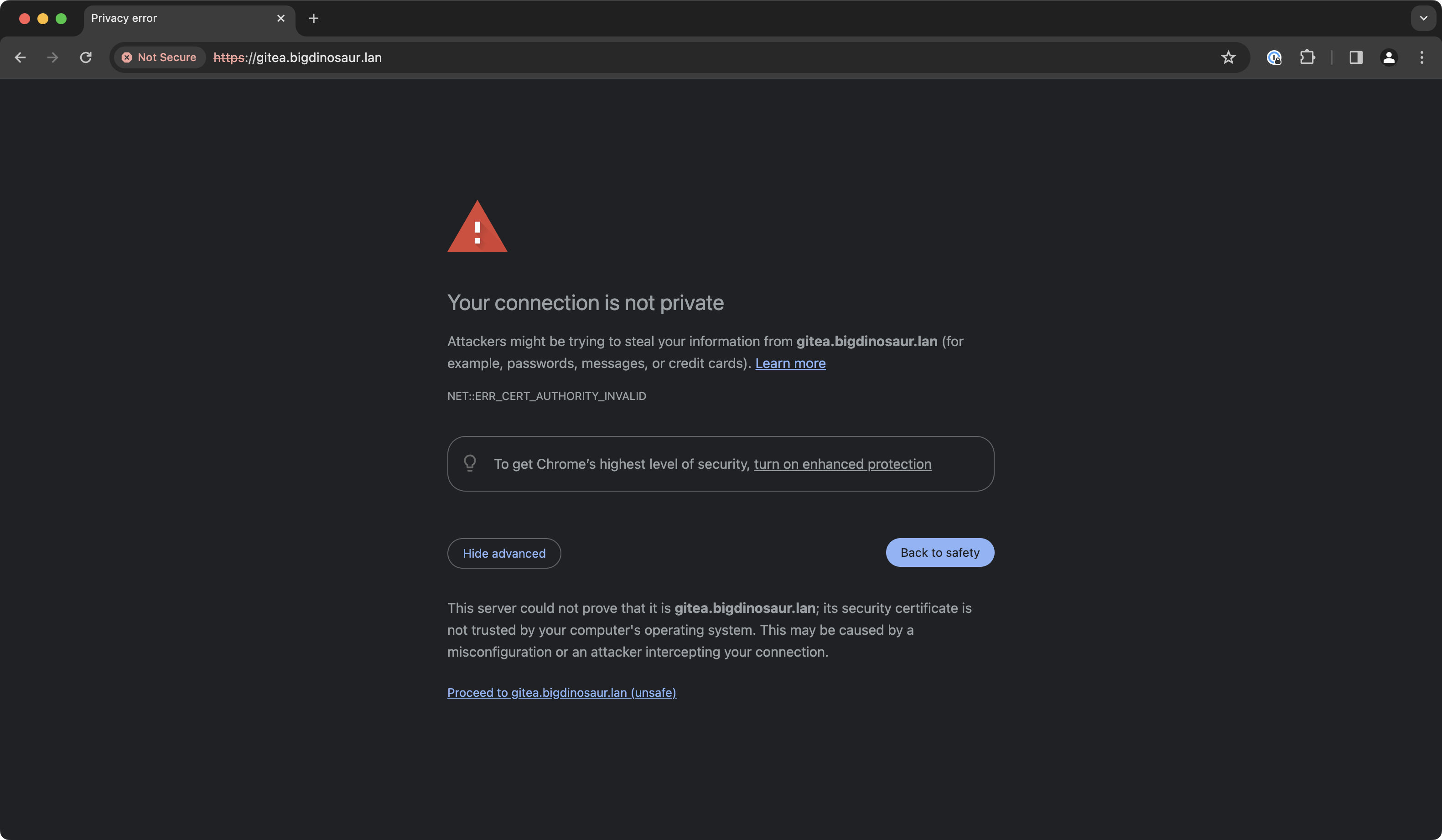
Lee Hutchinson
These warnings appear spurious, and most individuals rapidly grow to be blind to them, however they serve a vital goal—even when it is a goal lots of people do not care about.
See, internet browsers use TLS and HTTPS to attempt to accomplish two linked and equally essential issues: first, and most clearly, to encrypt the connection between you and the net useful resource you are accessing. However the second goal—the one upended by self-signed certs and the supply of the large warnings—is id verification. An assurance that your encrypted communication goes to the individual you assume it’ll is nearly as very important as having the communication encrypted within the first place.
A series of belief extends from the varied root certificates authorities down by way of the TLS certificates they situation to endpoints, and, a minimum of in concept, one ought to have the ability to belief {that a} CA has finished some quantity of due diligence to confirm the id and possession of the endpoints it points certificates to. Once you belief a certificates authority, you might be trusting that the id attestations on the certificates that CA points are the truth is correct—that seeing a cert for “www.instance.com” actually does imply you are looking “www.instance.com” and not a website pretending to be that (or that your connection is not being compromised through a man-in-the-middle kind assault).
Self-signed certificates break that chain of belief. Your browser has no option to validate that the useful resource is what its certificates says it’s, as a result of your browser does not belief the issuer.
Because of this browsers present large scary warnings whenever you go to a web page that presents a self-signed cert: You will have encryption, however no id verification. To banish the warnings, we’ve to have each—which is what we goal to supply with our step-ca set up. We’ll arrange our own CA and get it trusted by your browser and by the units and companies for which it’ll be issuing certificates.