In a bold and ambitious collaboration, Apple and Google are growing a smartphone platform that tries to track the unfold of the novel coronavirus at scale and at the identical time protect the privateness of iOS and Android customers who choose in to it.
The cross-platform system will use the proximity capabilities constructed into Bluetooth Low Vitality transmissions to track the bodily contacts of collaborating telephone customers. If a person later checks constructive for COVID-19, the illness attributable to the coronavirus, she will select to enter the outcome right into a well being department-approved app. The app will then contact all different collaborating telephone customers who’ve lately come inside six or so toes of her.
The system, which Google and Apple described right here and right here respectively, applies a technological method to what’s often called contact tracing, or the observe of determining everybody an contaminated particular person has lately been in touch with. A lately revealed examine by a bunch of Oxford researchers urged that the novel coronavirus is simply too infectious for contact tracing to work effectively utilizing conventional strategies. The researchers proposed utilizing smartphones, since they’re practically ubiquitous, don’t depend on defective reminiscences of people that have been contaminated, and can track a virtually limitless variety of contacts of different collaborating customers.
Mitigating the worst
However whereas mobile-based contact tracing could also be simpler, it additionally poses a critical risk to particular person privateness, because it opens the door to central databases that track the actions and social interactions of doubtless thousands and thousands, and presumably billions, of individuals. The platform Apple and Google are growing makes use of an revolutionary cryptographic scheme that goals to enable the contact tracing to work as scale with out posing a danger to the privateness of those that choose into the system.
Privateness advocates—with at least one notable exception—principally gave the system a certified approval, saying that whereas the scheme eliminated a number of the most speedy threats, it might nonetheless be open to abuse.
“To their credit score, Apple and Google have introduced an method that seems to mitigate the worst privateness and centralization dangers, however there’s nonetheless room for enchancment,” Jennifer Granick, surveillance and cybersecurity counsel for the American Civil Liberties Union, wrote in a press release. “We are going to stay vigilant transferring ahead to be certain that any contact tracing app stays voluntary and decentralized, and used just for public well being functions and solely all through this pandemic.”
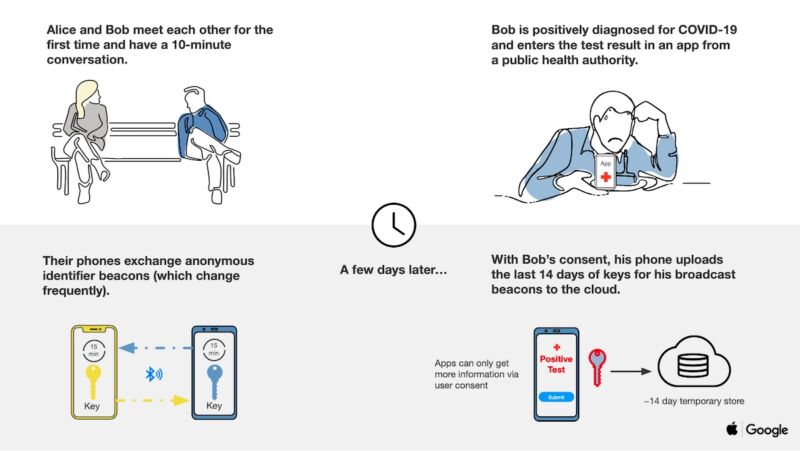
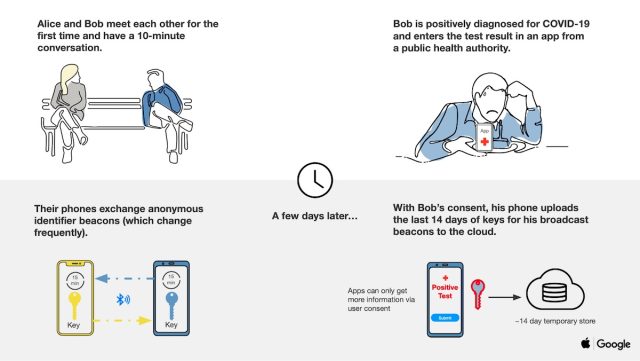
Not like conventional contact tracing, the telephone platform doesn’t acquire names, places, or different figuring out data. As an alternative, when two or extra customers opting into the system come into bodily contact, their telephones use BLE to swap nameless identifier beacons. The identifiers—which in technical jargon are often called rolling proximity identifiers—change roughly each 15 minutes to stop wi-fi monitoring of a tool.
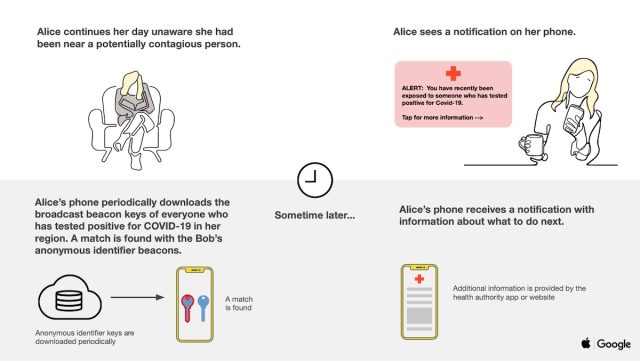
Because the customers transfer about and come into proximity with others, their telephones proceed to alternate these nameless identifiers. Periodically, the customers’ gadgets may even obtain broadcast beacon identifiers of anybody who has examined constructive for COVID-19 and has been in the identical native area.
Within the occasion somebody reviews to the system that she has examined constructive, her telephone will contact a central server and add 14 days of her identifiers. Non-infected customers obtain every day tracing keys, and due to the way in which every rolling proximity identifier is generated, end-user telephones can recreate them listed by time from simply the every day tracing key for every day. The next two slides assist illustrate at a excessive degree how the system works.
Apple and Google are offering different assurances, together with:
- Specific person consent required
- Doesn’t acquire personally identifiable data or person location information
- Record of individuals you’ve been in touch with by no means leaves your telephone
- Individuals who take a look at constructive aren’t recognized to different customers, Google or Apple
- Will solely be used for contact tracing by public well being authorities for COVID-19 pandemic administration
- Doesn’t matter when you have an Android telephone or an iPhone—works throughout each
The way it works (in principle)
Jon Callas, a cryptography knowledgeable and senior expertise fellow at the ACLU, instructed me that the scheme is analogous to the way in which raffle tickets work, with one celebration getting half of a paper ticket, the opposite celebration getting the opposite half, and—in principle at least—nobody else being the wiser. When two telephone customers come into bodily proximity, they BLE transmitters alternate tickets. Callas stated {that a} comparable COVID-19 monitoring scheme often called the Pan-European Privateness-Preserving Proximity Tracing seems to work roughly the identical manner.
“I preserve a listing of all of the tickets I’ve,” he stated. “If Alice checks constructive, she releases her tickets and if ones that I’ve match, I do know I had a contact with a constructive individual.” Callas went on to warning that ambiguities within the circulation of each the Apple-Google platform and the Pan-European Privateness-Preserving Proximity Tracing depart open the opportunity of abuse as a result of it’s not but clear which events get entry to which tickets.
“If Alice releases the tickets she despatched and those she obtained, she’s outing the individuals who have been close to her,” he stated.
Callas stated he was concerned in improvement of a 3rd monitoring scheme often called PACT, brief for Personal Automated Contact Tracing. Against this, he stated, it has assurances that events can solely launch despatched tickets.
Begging to differ
Moxie Marlinspike, a hacker and developer who has each damaged superior crypto schemes and constructed them, was among the many most vocal critics of the scheme as laid out. In a twitter thread that analyzed the way in which the APIs and cryptography interacted, he raised critical doubts in regards to the plan.
“So first apparent caveat is that that is ‘personal’ (or at least not worse than BTLE), *till* the second you take a look at constructive,” he wrote in one tweet. “At that time all your BTLE mac addrs [BLE MAC addresses] over the earlier interval change into linkable. Why do they modify to start with? As a result of monitoring is already an issue.”
So it takes BTLE privateness a ~step again. I do not see why all the current beacon monitoring tech would not incorporate this into their stacks.
At that time adtech (at minimal) in all probability is aware of who you might be, the place you’ve got been, and that you’re covid+.
— Moxie Marlinspike (@moxie) April 10, 2020
Marlinspike, who’s the creator of the Sign encrypted messenger app and the CEO of of the the corporate that stewards it, stated the following weak spot is the quantity of knowledge that may have to be transmitted to person telephones:
Second caveat is that it appears seemingly location information would have to be mixed with what the machine framework offers you.
Revealed keys are 16 bytes, one for every day. If average numbers of smartphone customers are contaminated in any given week, that is 100s of MBs for all telephones to DL
That appears untenable. So to be usable, revealed keys would seemingly want to be delivered in a extra ‘focused’ manner, which in all probability means… location information.
That appears untenable. So to be usable, revealed keys would seemingly want to be delivered in a extra ‘focused’ manner, which in all probability means… location information.
— Moxie Marlinspike (@moxie) April 10, 2020
One other doable weak spot: trolls would possibly frequent sure areas and then report a false an infection, main massive numbers of individuals to suppose they might have been uncovered. These sorts of malicious acts might be prevented by requiring take a look at outcomes to be digitally signed by a testing middle, however particulars launched on Friday, did not deal with these considerations. A variation of falsifying constructive outcomes is relaying BLE IDs collected from a hospital or different focused space.
Technologist and privateness advocate Ashkan Soltani supplied further privateness critiques in this Twitter thread:
In my view – these kind of information are poor proxies for the bottom reality we actually search: precise #COVID19 an infection charges — which might solely be really recognized by widespread testing. If we had testing in place, it could make the necessity to pursue these privacy-invasive methods moot
— ashkan soltani (@ashk4n) April 10, 2020
Soltani supplied different helpful particulars right here and right here.
Studying the specs
The cryptography behind the nameless and ever-changing identifiers are specified by this specification, which amongst different issues assures that:
- The important thing schedule is mounted and outlined by working system elements, stopping purposes
from together with static or predictable data that might be used for monitoring. - A person’s Rolling Proximity Identifiers can’t be correlated with out having the Each day Tracing Key. This
reduces the danger of privateness loss from promoting them. - A server operator implementing this protocol doesn’t be taught who customers have been in proximity with
or customers’ location except it additionally has the unlikely functionality to scan ads from customers who
lately reported Analysis Keys. - With out the discharge of the Each day Tracing Keys, it’s not computationally possible for an attacker to
discover a collision on a Rolling Proximity Identifier. This prevents a wide-range of replay and
impersonation assaults. - When reporting Analysis Keys, the correlation of Rolling Proximity Identifiers by others is restricted to
24h intervals due to using Each day Tracing Keys. The server should not retain metadata from shoppers
importing Analysis Keys after together with them into the aggregated record of Analysis Keys per day.
A separate Bluetooth specification, in the meantime, requires that:
- The Contact Tracing Bluetooth Specification doesn’t require the person’s location; any use of location is totally non-obligatory to the schema. In any case, the person should present their specific consent to ensure that their location to be optionally used.
- Rolling Proximity Identifiers change on common each 15 minutes, making it unlikely that person location may be tracked through bluetooth over time.
- Proximity identifiers obtained from different gadgets are processed solely on machine.
- Customers determine whether or not to contribute to contact tracing.
- If identified with COVID-19, customers consent to sharing Analysis Keys with the server.
- Customers have transparency into their participation in touch tracing.
Coming to a telephone close to you
Apple and Google plan to launch iOS and Android programming interfaces in Might. They are going to be out there public well being authorities for growing apps working on one cell working system to work with apps working on the opposite. The official apps will then be out there for obtain in Apple’s App Retailer and Google Play. Finally, the businesses plan to introduce tracing performance straight into the OSes. Presumably, customers can activate the performance with a setting change.
Moreover the privateness dangers, there are different potential flaws. The system may trigger undue alarm if it sends a warning that somebody was uncovered, when in truth the opposite celebration was dwelling in the identical residence constructing however in separate models. Bluetooth can be susceptible to a wide range of flaws that may compromise its reliability and often its safety.
There are numerous essential particulars that aren’t but out there and are essential to understanding the privateness dangers of the system Apple and Google are constructing. In regular instances, it is perhaps a given to advise individuals to choose out. Given the worldwide well being disaster introduced by the continued pandemic, the decision might be a lot tougher to make this time round.
Submit up to date to right the data uploaded from the telephone of somebody who checks constructive.