

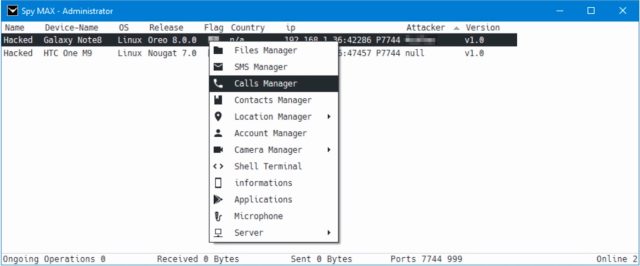
Researchers have uncovered a cellular surveillance marketing campaign that has used greater than 30 malicious Android apps to spy on targets over the previous 11 months. Two of the most up-to-date samples are exploiting the coronavirus by hiding off-the-shelf surveillanceware inside apps that promise to supply details about the ongoing pandemic.
One in every of the apps, “corona dwell 1.1,” is a trojanized model of “corona dwell,” a reliable app that gives an interface to information discovered on this tracker from Johns Hopkins College. Buried inside the spoofed app is a pattern of SpyMax, a commercially accessible piece of surveillanceware that provides attackers real-time management of contaminated units. A second app utilized in the identical marketing campaign is known as “Crona.” The marketing campaign, which has been energetic since April 2019 at the newest, was found by researchers from mobile-security supplier Lookout.
“This surveillance marketing campaign highlights how in occasions of disaster, our innate want to hunt out data can be utilized towards us for malicious ends,” Lookout researcher Kristin Del Rosso wrote in a put up revealed on Wednesday. “Moreover, the commercialization of off-the-shelf’ adware kits makes it pretty straightforward for these malicious actors to spin up these bespoke campaigns nearly as rapidly as a disaster like COVID-19 takes maintain.”
Lookout researchers uncovered the ongoing marketing campaign when analyzing “corona dwell 1.1.” Whereas the app gave the impression to be in the early phases of improvement, it had a hard-coded deal with of its management server. When analyzing the management server area, the researchers discovered that it was being utilized by 29 or so different apps, all of which additionally used commercially accessible surveillanceware choices to spy on finish customers.
The most recent pattern was ingested on Tuesday, and command and management servers appeared to stay on-line at the time this put up was going dwell on Ars. Lookout stated the apps have been by no means accessible in the Google Play market. Lookout has but to find out how the apps are distributed or what number of units have been contaminated.
DIY spy
Whereas most of the apps have been packaged utilizing pretty generic names, certainly one of them—“Libya Cell Lookup”—hinted that the marketing campaign could also be concentrating on folks in the North African nation. The management server beforehand resolved to IP addresses operated by Libyan Telecom and Know-how, a shopper ISP. The attackers hosted the server with the use of No-IP, a service that makes it straightforward for shoppers or very small operations to hyperlink Web domains to IP addresses that steadily change.
“The particular person or group operating the marketing campaign is probably going in Libya and utilizing their very own infrastructure to run the C2, or is leveraging infrastructure they’ve compromised there,” Del Rosso wrote. “As the functions are additionally particularly aimed toward Libyan customers, this seems to be a regionally focused surveillance effort.”
Lookout isn’t the solely safety agency to trace malicious Android wares that exploit coronavirus anxieties. On Wednesday, antivirus supplier Avast stated it was unveiling apklab.io, a useful resource that permits researchers to contribute and look at Android malware with themes associated to the pandemic. The location presently tracks greater than 450 APKs. Final week, researchers at Area Instruments disclosed the existence of one other malicious Android app that additionally claimed to supply maps associated to the virus.
SpyMax seems to be developed by the identical folks behind one other commercially accessible piece of surveillanceware referred to as SpyNote. Different surveillanceware utilized in the marketing campaign consists of SonicSpy, SandroRat, and MobiHok. Each SpyNote and MobiHok cost comparatively low charges and likewise supply person assist. Mixed with a simple checkout course of, the apps make it straightforward for even novices to accumulate, customise, and handle their very own surveillance instruments.
Lookout
Lookout has no proof that hackers working for a nation-state are working the marketing campaign. The safety firm, nonetheless, didn’t rule out that chance, since nation-states have beforehand been seen utilizing out-of-the-box instruments or malware from each open supply and business sources. Then once more, nation-states usually develop their very own instruments. The underside line is that there’s no manner to make certain what sort of group is behind the marketing campaign.
The latest additions of coronavirus-themed trojans to this ongoing marketing campaign underscores how fast attackers are to use main information occasions. Readers are as soon as once more reminded to stay extremely skeptical of apps, maps, or different data associated to the pandemic, significantly when these accessible for Android come from third-party markets. Folks ought to as an alternative search data from trusted sources comparable to this web page from the US Facilities for Illness Management and Prevention or the above-linked Johns Hopkins useful resource.