

Secure Boot is an business commonplace for making certain that Home windows units don’t load malicious firmware or software program throughout the startup course of. In case you have it turned on—as you need to usually, and it is the default setting mandated by Microsoft—good for you. In case you’re utilizing one of greater than 300 motherboard models made by producer MSI prior to now 18 months, nevertheless, you might not be protected.
Launched in 2011, Secure Boot establishes a series of belief between the {hardware} and software program or firmware that boots up a tool. Previous to Secure Boot, units used software program generally known as the BIOS, which was put in on a small chip, to instruct them tips on how to boot up and acknowledge and begin exhausting drives, CPUs, reminiscence, and different {hardware}. As soon as completed, this mechanism loaded the bootloader, which prompts duties and processes for loading Home windows.
The issue was: The BIOS would load any bootloader that was situated within the correct listing. That permissiveness allowed hackers who had temporary entry to a tool to put in rogue bootloaders that, in flip, would run malicious firmware or Home windows pictures.
When Secure Boot falls aside
A couple of decade in the past, the BIOS was changed with the UEFI (Unified Extensible Firmware Interface), an OS in its personal proper that would stop the loading of system drivers or bootloaders that weren’t digitally signed by their trusted producers.
UEFI depends on databases of each trusted and revoked signatures that OEMs load into the non-volatile reminiscence of motherboards on the time of manufacture. The signatures listing the signers and cryptographic hashes of each licensed bootloader or UEFI-controlled software, a measure that establishes the chain of belief. This chain ensures the machine boots securely utilizing solely code that’s recognized and trusted. If unknown code is scheduled to be loaded, Secure Boot shuts down the startup course of.
A researcher and pupil not too long ago found that greater than 300 motherboard models from Taiwan-based MSI, by default, aren’t implementing Secure Boot and are permitting any bootloader to run. The models work with numerous {hardware} and firmware, together with many from Intel and AMD (the complete listing is right here). The shortcoming was launched someday within the third quarter of 2021. The researcher unintentionally uncovered the issue when trying to digitally signal numerous parts of his system.
“On 2022-12-11, I made a decision to setup Secure Boot on my new desktop with a assist of sbctl,” Dawid Potocki, a Poland-born researcher who now lives in New Zealand, wrote. “Sadly I have discovered that my firmware was… accepting each OS picture I gave it, irrespective of if it was trusted or not. It wasn’t the primary time that I have been self-signing Secure Boot, I wasn’t doing it fallacious.”
Potocki stated he discovered no indication motherboards from producers ASRock, Asus, Biostar, EVGA, Gigabyte, and NZXT endure the identical shortcoming.
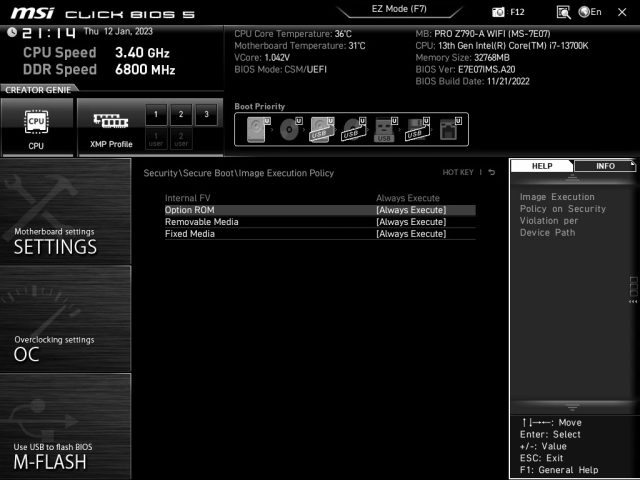
The researcher went on to report that the damaged Secure Boot was the outcome of MSI inexplicably altering its default settings. Customers who need to implement Secure Boot—which actually ought to be everybody—should entry the settings on their affected motherboard. To try this, maintain down the Del button on the keyboard whereas the machine is booting up. From there, choose the menu that claims SecuritySecure Boot or one thing to that impact after which choose the Picture Execution Coverage submenu. In case your motherboard is affected, Detachable Media and Fastened Media might be set to “At all times Execute.”
Getty Photos
To repair, change “At all times Execute” for these two classes to “Deny Execute.”
In a Reddit put up printed on Thursday, an MSI consultant confirmed Potocki’s findings. The consultant wrote:
We preemptively set Secure Boot as Enabled and “At all times Execute” because the default setting to supply a user-friendly setting that permits a number of end-users flexibility to construct their PC techniques with 1000’s (or extra) of parts that included their built-in choice ROM, together with OS pictures, leading to increased compatibility configurations. For customers who’re extremely involved about safety, they will nonetheless set “Picture Execution Coverage” as “Deny Execute” or different choices manually to fulfill their safety wants.
The put up stated that MSI will launch new firmware variations that may change the default settings to “Deny Execute.” The above-linked subreddit comprises a dialogue which will assist customers troubleshoot any issues.
As talked about, Secure Boot is designed to forestall assaults during which an untrusted particular person surreptitiously will get temporary entry to a tool and tampers with its firmware and software program. Such hacks are normally generally known as “Evil Maid assaults,” however a greater description is “Stalker Ex-Boyfriend assaults.”